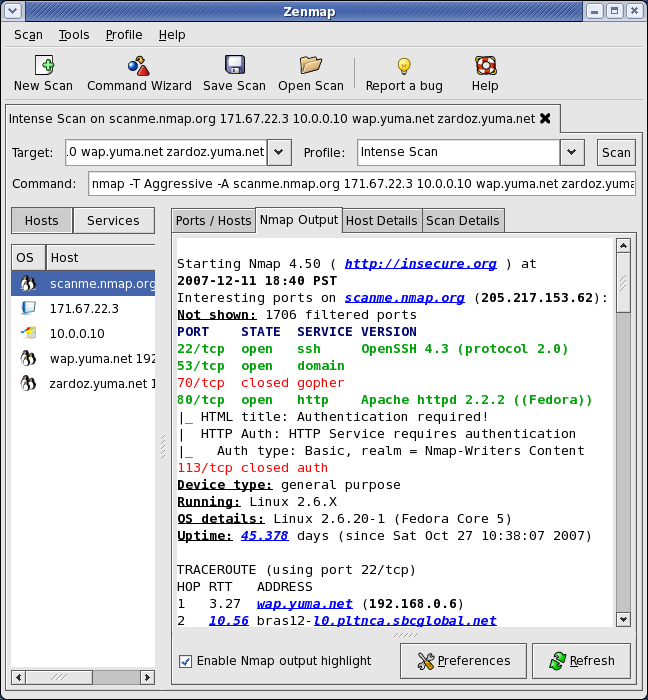
Nmap Zombie. I hope i got your questions right cause i still have doubts about whether this is what you want exactly. OS CPE This shows a Common Platform Enumeration (CPE) representation of the operating system when available. Besides being extraordinarily stealthy, this scan type permits discovery of IP-based trust relationships between machines. However, prior to using the Nmap zombie scan, we can quickly find any viable zombie candidates by sweeping an entire address range and assessing the IPID sequencing patterns with Metasploit. If a response is received, it is assumed that the port is open. -sI <zombie host>[:<probeport>]. a colon followed by a port number to the zombie host if you wish to probe a particular port on the zombie for IP ID changes. These steps will help you to perform a zombie scan on the Nmap: Zombie scans can also be performed with an option in Nmap. For more about CPE see the section called "Common Platform Enumeration (CPE)". To use Nmap to perform a zombie scan, you will need to have a remote system that is running TCP services and another remote system that has incremental IPID sequencing.
Nmap Zombie. Nmap NSE (Nmap Scripting Engine) comes with a handy script called IPIDSEQ. Nmap ("Network Mapper") is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. We are attacking the target machine using a zombie host. To implement a zombie scan, you must have the following two requirements. Nmap Zombie.
It may also have a CPE representation of the hardware type.
I hope i got your questions right cause i still have doubts about whether this is what you want exactly.
Nmap Zombie. OS CPE This shows a Common Platform Enumeration (CPE) representation of the operating system when available. Which we can use to scan for random zombies on the internet. Besides being extraordinarily stealthy, this scan type permits mapping out IP-based trust relationships between machines. If a response is received, it is assumed that the port is open. -sI <zombie host>[:<probeport>]. a colon followed by a port number to the zombie host if you wish to probe a particular port on the zombie for IP ID changes. I assumed that a problem of this magnitude would generate an immediate response and patches from the OS vendors.
Nmap Zombie.