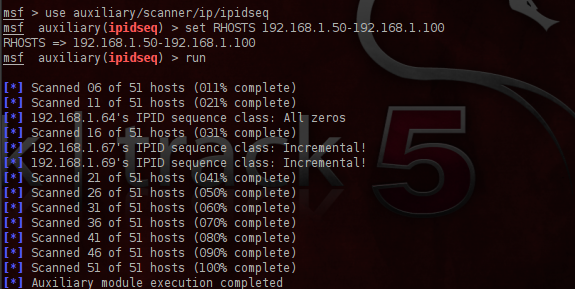
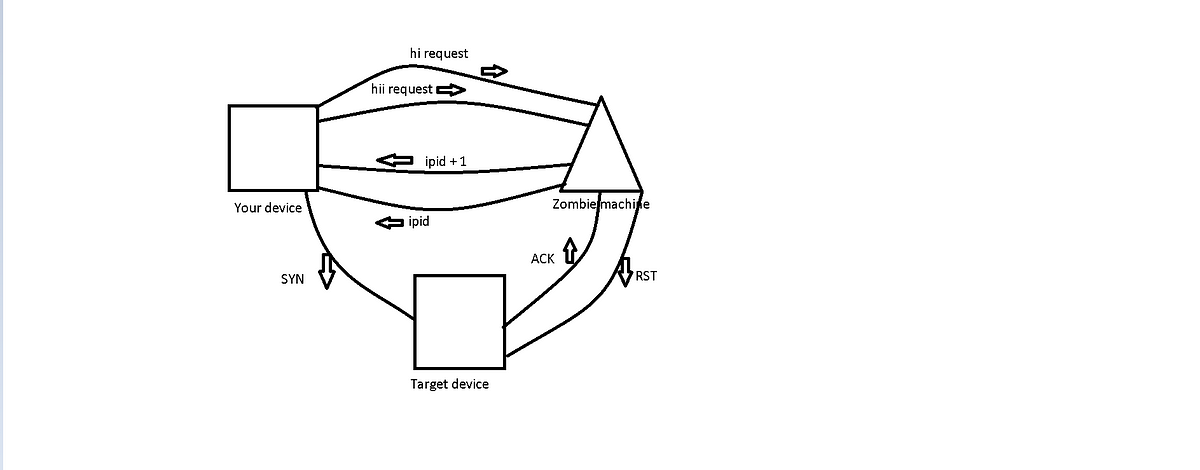
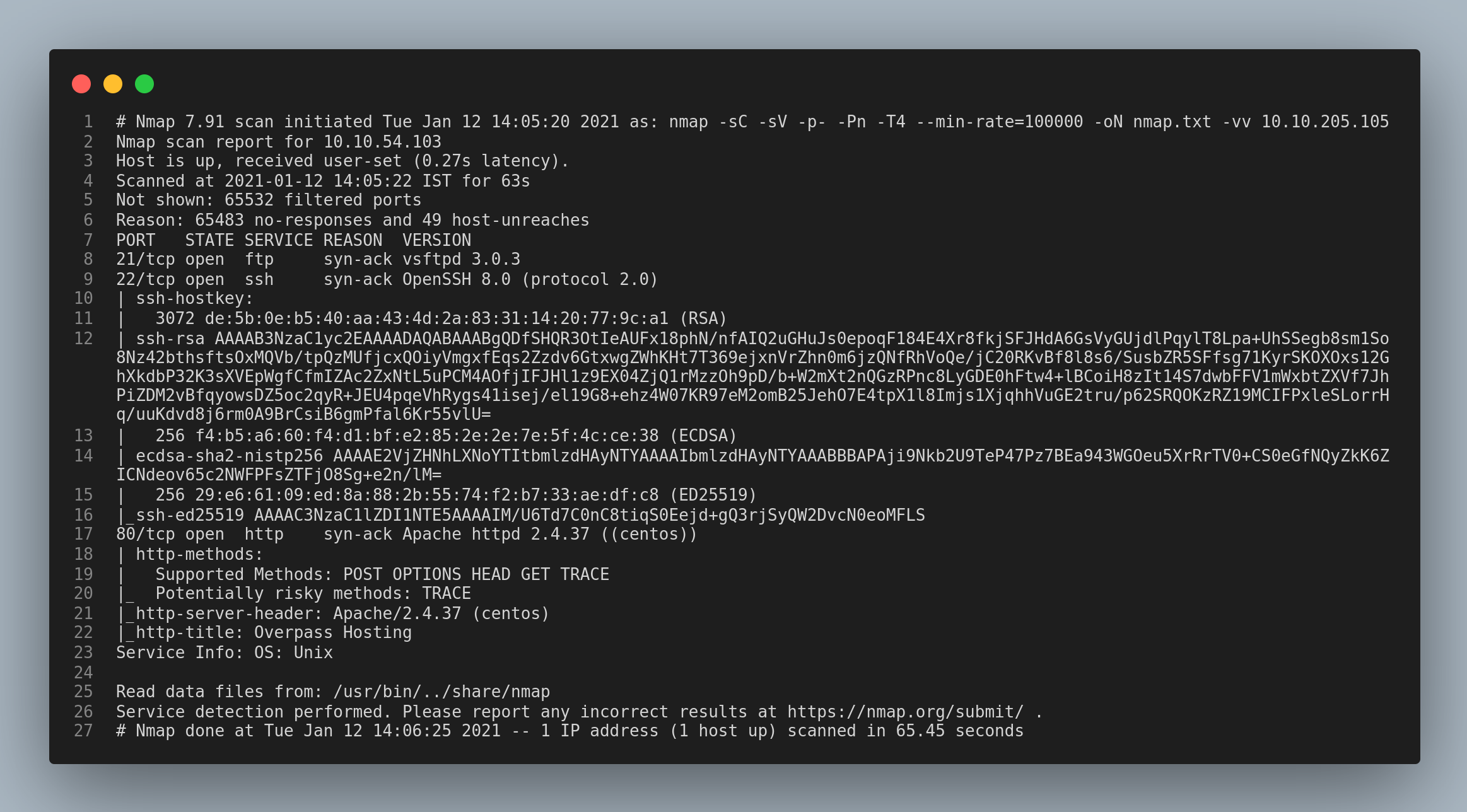
Nmap Zombie Scan. I tried to perform an idle scan in Nmap but it only takes one IP address as a zombie at a time. If a response is received, it is assumed that the port is open. No packet is sent from its own IP address, instead, another host is used called Zombie. I want to perform port scan against a target but the firewall at the target only allows traffic to the ports through certain IP address/machines. It explain that you must find a host with IPID sequences of either Incremental or Broken little-endian incremental. This technique is easiest to describe via a diagram. To perform a zombie scan using Nmap, the following command can be used: nmap – sI < zombie_ip > <target_ip> shell Here, the `-sI` option is used to specify the IP address of the zombie system. This is accomplished by impersonating another computer.
Nmap Zombie Scan. If a response is received, it is assumed that the port is open. It explain that you must find a host with IPID sequences of either Incremental or Broken little-endian incremental. TCP SYN scan Earn two pentesting certifications at once! I want to perform port scan against a target but the firewall at the target only allows traffic to the ports through certain IP address/machines. Send a SYN packet to a TCP port on the. Nmap Zombie Scan.
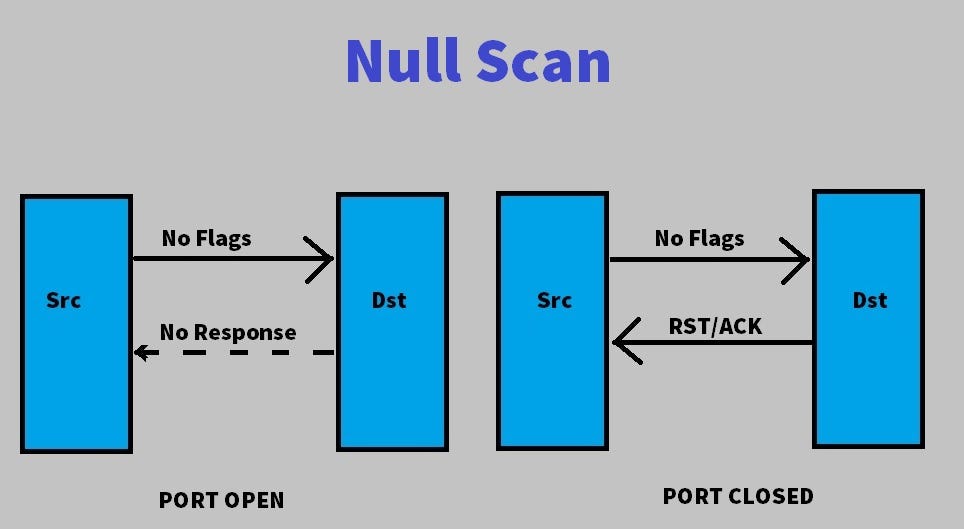
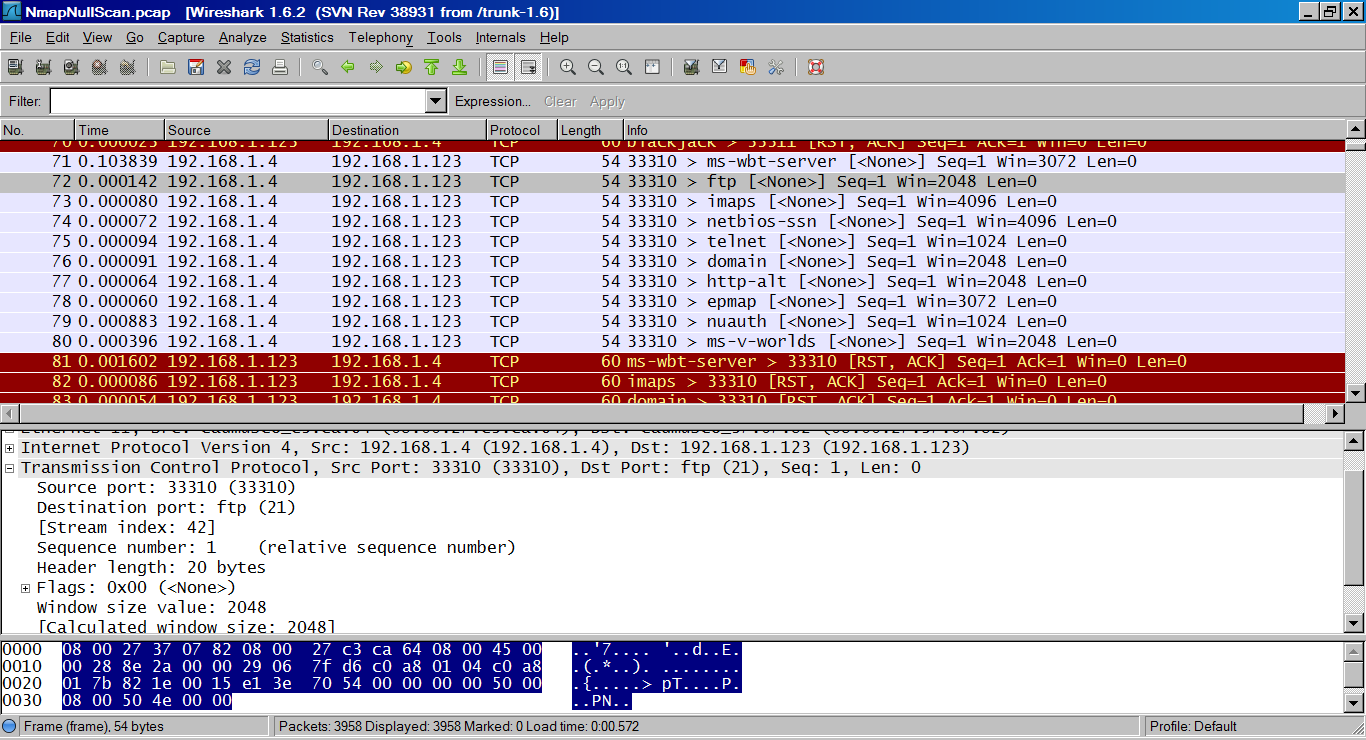
It is also relatively unobtrusive and stealthy since it never completes TCP connections.
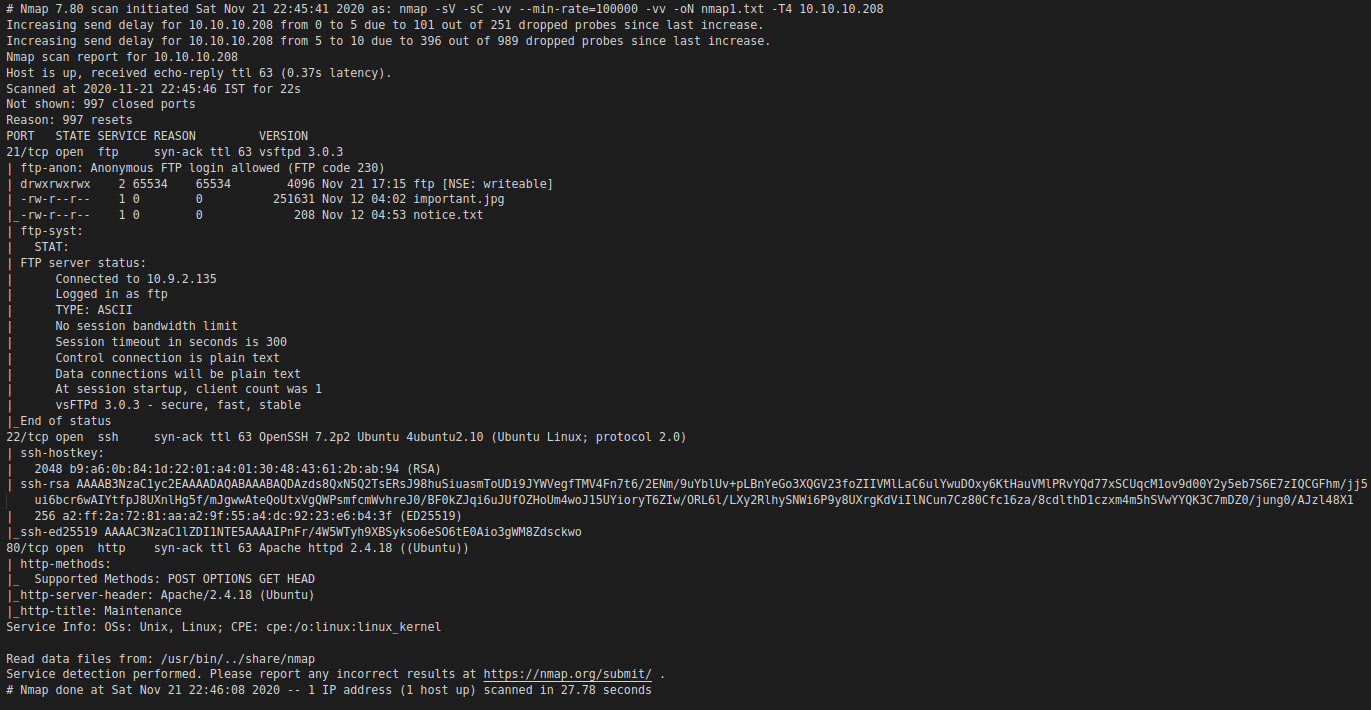
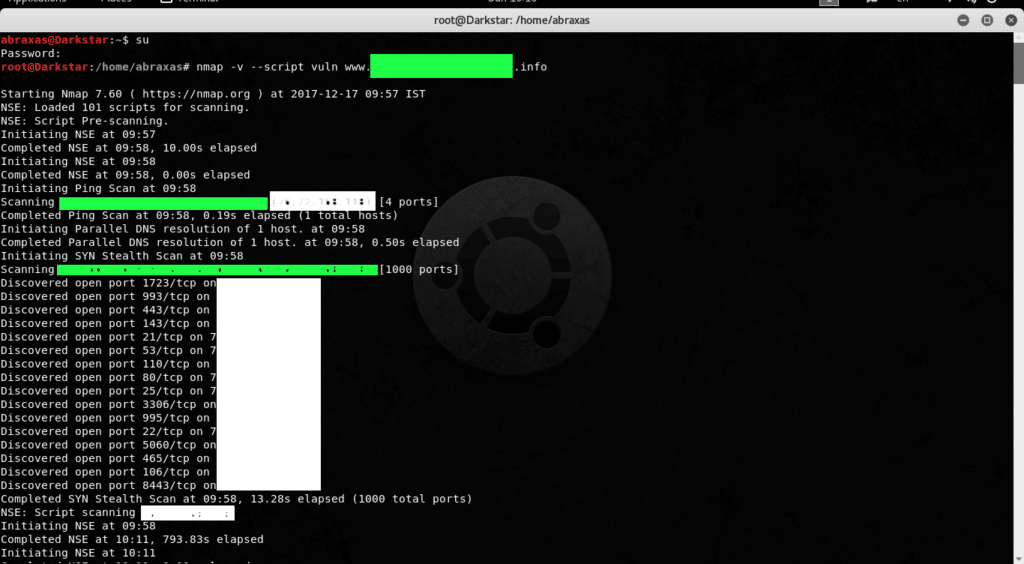
In this video we are going to see how you can use NMAP Zombie scan technique to scan a host secretly.
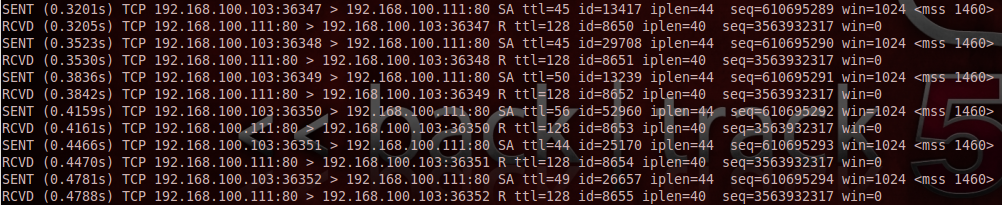
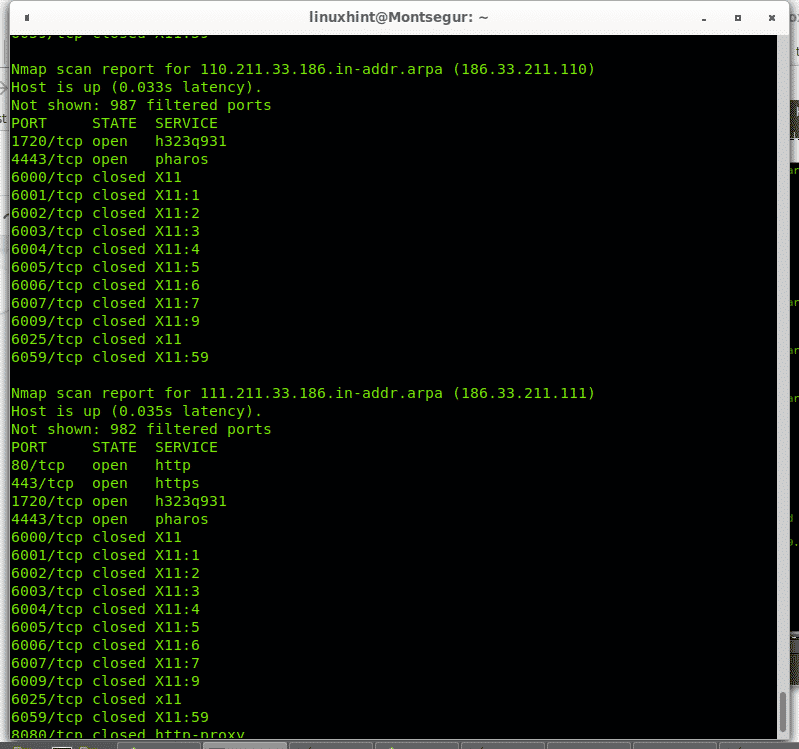
Nmap Zombie Scan. Nmap ("Network Mapper") is a free and open source utility for network discovery and security auditing. In the picture below, an attacker, A, is scanning a Target machine, while blaming the scan on some Zombie, Z. After this process, the zombie's IP ID should have increased by either one or two. Basically, we will discuss some advanced techniques for Nmap scanning and we will conduct a Man In The Middle Attack (MITM). Nmap will send SYN packets to the target system with the zombie's IP address as the source.
Nmap Zombie Scan.